Stirring, Mixing, Blending: Different Approaches to Proposer Anonymity
Proposer anonymity strategies can be compared to the ways a drink is made: by stirring, mixing, or blending.

An important aspect of building a privacy-preserving peer-to-peer network is ensuring that not just the contents of messages, but also their senders and receivers, cannot be easily revealed. To protect against global adversaries that are able to monitor the entire network’s activity, the path a message takes must be difficult to distinguish from other messages’ paths. This strategy of “hiding in the crowd” is the key insight behind modern mixnets, and can be accomplished with a variety of approaches - each of which builds on its predecessor to enhance its anonymity properties.
Much like a good bartender, who combines spirits and tonics to make a drink with a uniform taste, a network employing anonymisation techniques ensures that individual messages cannot be distinguished. The three anonymisation strategies described in this article can therefore be compared to three ways a drink is made: by stirring, mixing, or blending.
For Nomos in particular, an anonymous broadcasting protocol is necessary to reduce the probability of linking a block proposal to its proposer, thereby enhancing the privacy properties achieved by its Private Proof of Stake consensus protocol. Based on the blending strategy, the Nomos Blend Network was designed to provide the necessary anonymity to consensus leaders while minimising bandwidth usage. The reasons why Nomos used a custom-built blending protocol instead of a general-use mixnet will also be explored.
“Stirring” - Onion Routing
The most basic level of anonymisation is achieved with “stirring”, more correctly referred to as onion routing. This strategy involves sending the message along a predetermined path of nodes before reaching the intended receiver, with the message being progressively decrypted by each node in the path. The layers of encryption are like the layers of an onion, hence the name. Onion routing is perhaps most famous for being used by the Tor project, and basically works as follows:
- The message sender first selects a random path of nodes along which they will relay their message to the receiver.
- The sender encrypts the message payload in a way that the receiver can decrypt it.
- The sender encrypts this encrypted message again for node n in the path, and the result will be encrypted further for node n-1, then again for node n-2, and so on until the first node in the path. These layers of encryption at each stage ensure that only the intended node can send a message further along.
- When the sender sends this layered message, each node in the path progressively decrypts it and send the result to the next node in the path.
- When the receiver finally receives their message, they decrypt it and are able to retrieve the original payload.
This process is depicted in Figure 1.
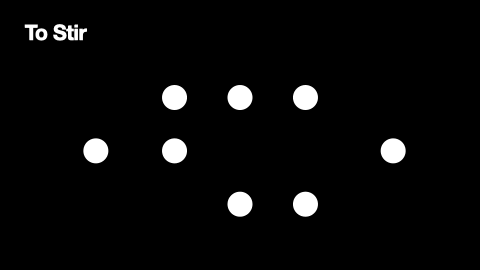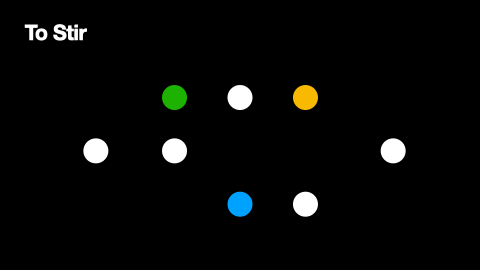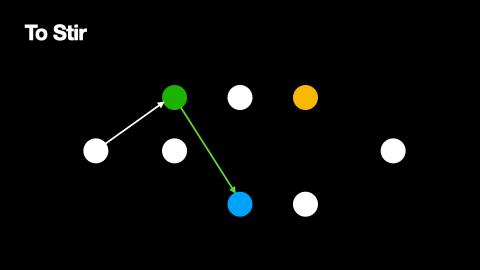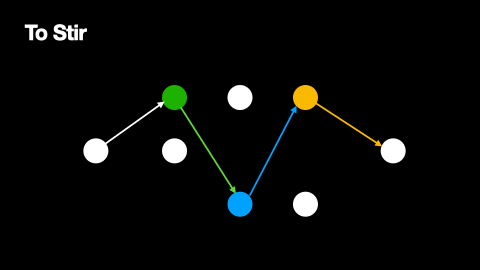
Compared to the direct transmission of a message from sender to receiver, sending a message via onion routing makes the sender and receiver of a message more difficult to detect. This is because, when a message is seen, it is not clear what its source and destination are. Due to the layered encryption, even the message’s position on its path is not apparent to observers - so long as at least one node on the path is acting honestly. The source of anonymity for this strategy is the layered transmission path, where the number of nodes on the path decreases the likelihood of deanonymisation.
However, the anonymity provided by onion routing alone is limited. While the network may appear chaotic and message paths may overlap, simply monitoring when messages are sent and received can be used to learn who sent a message. For example, if two senders send messages one after the other, and a receiver receives two messages, the first message to be received will be the message that was sent first. Additionally, if message paths do not overlap, network analysis can be used to determine the source and destination of each message. These vulnerabilities make onion routing inadequate for the purposes of the Nomos Network.
Mixing
The mixing strategy, used by mix networks, builds upon onion routing by adding random delays at each node in the path. This delay means that the order in which messages are received no longer necessarily corresponds to the order in which they were sent. Nodes in a mix network are arranged into layers, with each node receiving messages from nodes in the previous layer and sending messages to nodes in the next layer.
Additionally, mix networks employ cover traffic to further obscure message patterns. Cover traffic consists of dummy messages that nodes send to the next network layer even when they have no real messages to relay. This ensures that there is constant network activity, making it harder for observers to identify when genuine messages are being transmitted. The effectiveness of cover traffic is particularly important in situations where message paths do not overlap, as these paths would otherwise be vulnerable to traffic analysis. The way cover traffic obscures genuine message paths can be understood from Figures 2 and 3.
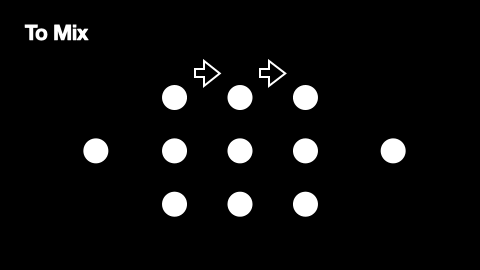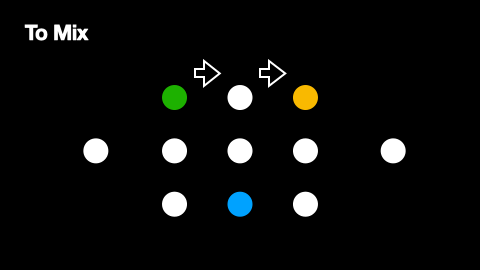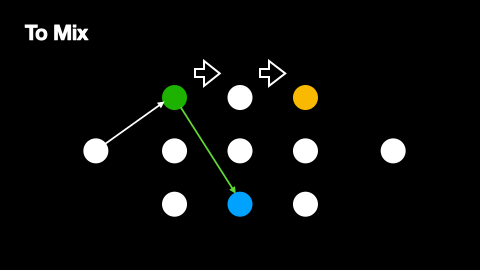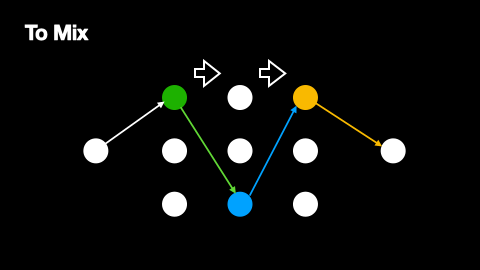
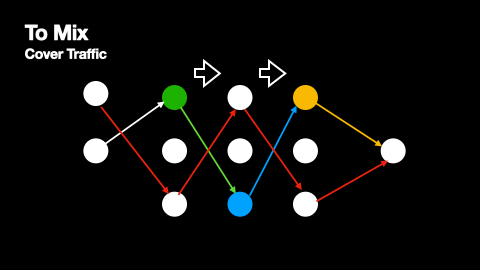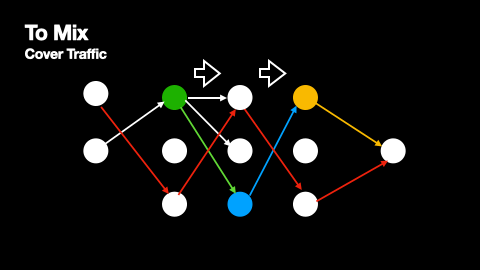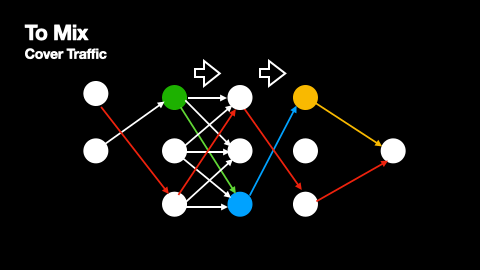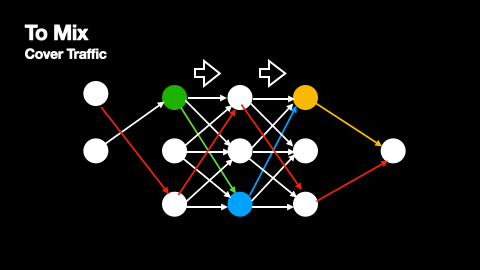
The primary source of anonymity in mix networks comes from multiple senders routing their messages through the same mix nodes. When several messages arrive at a mix node, they are held for a random period before being forwarded, effectively "mixing" them together and making it difficult to correlate incoming and outgoing messages. As a node receiving a genuine message will also receive several dummy messages from the previous layer, every point in a message’s path produces and compounds this anonymisation effect.
Despite this additional anonymity, mix networks face a significant challenge: in many applications, genuine messages are relatively rare compared to the cover traffic. Since senders and receivers are not part of the mix network itself, an adversary can view it as a “black box” with inputs and outputs occurring fairly rarely. Even with randomised delays at each layer, an adversary can identify senders and receivers with high probability because there are few (if any) other actors at any given time.
Blending
The blending strategy takes a different approach to anonymity by requiring both senders and receivers to be active participants in the network. Instead of trying to hide message paths through intermediate nodes, blend networks uses broadcasting: messages are sent to all nodes in the network. This strategy shifts the source of anonymity from having multiple senders transmitting to a single node (as in mixing) to having one node transmitting to multiple receivers. When a message is broadcast to all nodes, observers cannot determine which node was the intended receiver, even if they can identify the sender.
The process of transmitting a message through a blend network is similar to that of a mix network, with some key differences. It proceeds as follows:
- The message sender selects a random path of nodes along which it will relay its message to the receiver, covering the message in layers of encryption for every node on the path.
- The sender sends the layered message to every node with which it maintains a peer-to-peer connection.
- When a blend node receives a message, it checks that the message is unique and has not yet been seen, relaying it to its own peers. This ensures that every message is ultimately disseminated to the entire network.
- A blend node that receives a message will also attempt to decrypt the message. If it is able to decrypt the outer layer of a message it receives, it relays this decrypted message (after a randomised delay) to its peers for the next node in the path to receive and decrypt.
- When the receiver finally receives its message, it decrypts this message and is able to retrieve the original payload.
At the same time as messages are being broadcasted, nodes produce cover traffic that they broadcast to their peers just like genuine messages. This process is depicted in Figures 4 and 5.
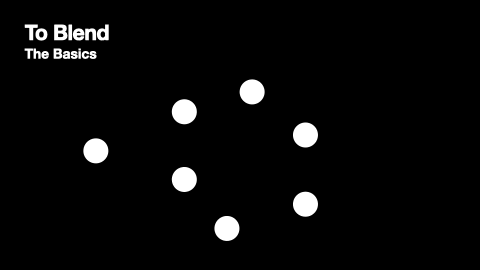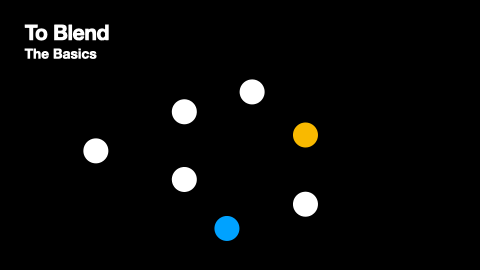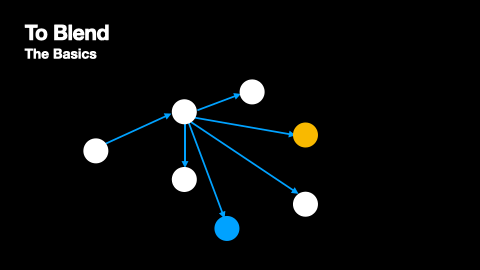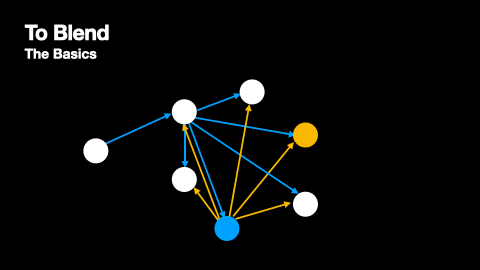
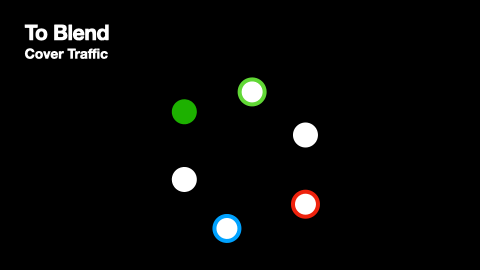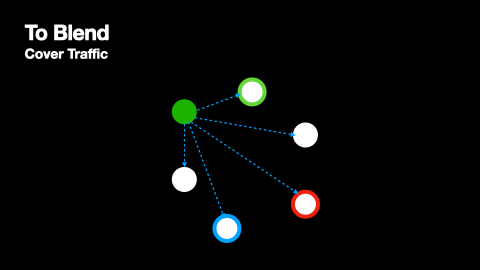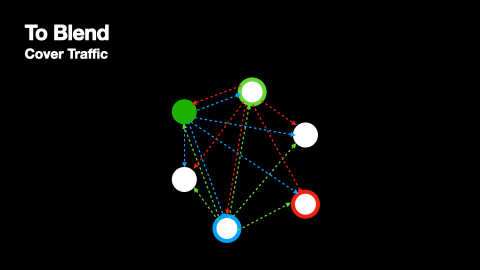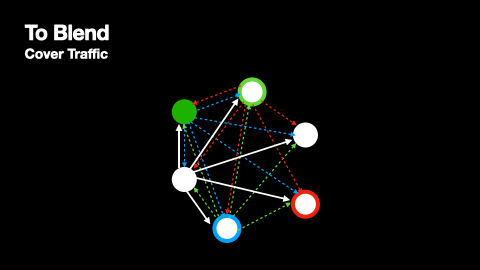
Nomos Blend Network
The Nomos Blend Network uses a custom Blend Protocol in order to reduce the probability of linking a block proposal with its proposer in an environment when block proposals are rare. Within the context of Nomos’ Private Proof of Stake consensus, this guarantee also translates to increasing the difficulty of learning a proposer’s relative stake. While PPoS on its own only hides the proposer’s identity before they propose a block, the Blend Network ensures that a proposer’s identity remains hidden both before and after a proposal.
In order to achieve a robust level of proposer anonymity within a highly decentralised environment and with low bandwidth usage, it was necessary to design a protocol tailored to the Nomos Network rather than rely on a general-use mix network. However, to achieve these properties, the Blend Network must operate with high latency. This is due to the Anonymity Trilemma, which states that a system can have at most two properties from the following: strong anonymity, low bandwidth usage, and low latency.
In brief, the Nomos Blend Protocol consists of four components, all of which work together to enhance the anonymity of block proposers. These are:
- Message Blending: Cryptographically decrypts messages and randomly delays their propagation to reduce the likelihood of linking incoming and outgoing messages based on their content or sending time.
- Cover Traffic: Introduces cover messages that are encrypted and transmitted along a path in the same way as true data messages, mimicking real traffic.
- Economic Incentives: Provides a privacy-preserving participation measurement mechanism in order to reward nodes based on their contribution to the Blend Protocol.
- Reliable Communication: Introduces a level of redundancy of communication through message replication and erasure coding. This module is meant to decrease the probability of a communication failure by adding resilience to the Blend Network.
As a result of these modules, the Blend Network provides strong anonymity guarantees to block proposers and ensures incentives are aligned.
Conclusion
“Stirring”, mixing, and blending represent different ways to ensure message anonymity, each leveraging various strategies to protect against adversaries monitoring network activity. While onion routing provides basic path obfuscation through layered encryption, it remains vulnerable to timing analysis. Mixing addresses this vulnerability by introducing random delays and cover traffic, but struggles when genuine messages are sparse. Blending takes a different approach by making all participants active in the network and using broadcasting to change the source of its anonymity.
The Nomos Network's choice to implement a custom Blend Protocol reflects its specific requirements. While this decision necessitates accepting higher latency, it enables the network to achieve strong proposer anonymity and stake privacy while maintaining reasonable bandwidth usage. This trade-off aligns with Nomos' focus on privacy and decentralisation, demonstrating how anonymity strategies can be adapted to serve specific use cases effectively.

